Many phishing messages go undetected without advanced cybersecurity measures in place. If the answer is helpful, please click "Accept Answer" and kindly upvote it. Here are some tips for recognizing a phishing email: Subtle misspellings (for example, micros0ft.com or rnicrosoft.com). This gives them an opportunity to modify allows and blocks as needed. You can then select Internet Explorer: While you're on a suspicious site, select the gear icon, point to Safety, and then select Report Unsafe Website. You can't override the From address requirements for outbound email that you send from Microsoft 365. This example changes spoofed sender entry from allow to block. Follow the instructions on the webpage that displays to report the website. If you suddenly receive an email from an entity or a person you rarely deal with, consider this email suspect. Azure Active Directory part of Microsoft Entra, Microsoft Defender Vulnerability Management, Microsoft Defender Cloud Security Posture Mgmt, Microsoft Defender External Attack Surface Management, Microsoft Purview Insider Risk Management, Microsoft Purview Communication Compliance, Microsoft Purview Data Lifecycle Management, Microsoft Security Services for Enterprise, Microsoft Security Services for Modernization. Social engineering attacks are designed to take advantage of a user's possible lapse in decision-making. After the add-in is installed and enabled, users will see the following icons: The Report Message icon in the Classic Ribbon: The Report Message icon in the Simplified Ribbon: Click More commands > Protection section > Report Message. Another prevalent phishing approach, this type of attack involves planting malware disguised as a trustworthy attachment (such as a resume or bank statement) in an email. You get the Ids parameter value from the Identity property in the output of Get-TenantAllowBlockListSpoofItems command. They are not logging into your account. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. By default, allow entries for domains and email addresses, files, and URLs exist for 30 days. The following From email addresses are invalid: From:  To keep your data safe, operate with intense scrutiny or install email protection technology that will do the hard work for you. By default, allow entries for spoofed senders never expire. For more information, see Submit files for analysis. Usage tab: The chart and details table shows the number of active users over time. To view an email timeline, click on the subject of an email message, and then click Email timeline. For more information, see Permissions in the Microsoft 365 Defender portal. Then I click the "report the user", it reply to "safety-team@hotmail.com", I had 3 of those emails last week. Using various layers of filtering, EOP can provide different controls for spam filtering, such as bulk mail controls and international spam, that will further enhance your protection services. On the Review and finish deployment page, review your settings. To bypass the From address requirements for inbound email, you can use the IP Allow List (connection filtering) or mail flow rules (also known as transport rules) as described in Create safe sender lists in Microsoft 365. Remember, phishing emails are designed to appear legitimate. The following values are available in the Filter flyout that appears: When you're finished, click Apply. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Here are the possible values of delivery location: Email Timeline is a field in Threat Explorer that makes hunting easier for your security operations team. Then go to the organization's website from your own saved favorite, or via a web search. If the From address includes a display name, the EmailAddress value must be enclosed in angle brackets (< >) as shown. If you regularly receive email from organizations that have malformed From addresses as described in this article, encourage these organizations to update their email servers to comply with modern security standards. Remove block entry after: The default value is 30 days, but you can select from the following values: Optional note: Enter descriptive text for why you're blocking the email addresses or domains. Confirm that youre using multifactor (or two-step) authentication for every account you use. The Microsoft Report Message and Report Phishing add-ins for Outlook and Outlook on the web (formerly known as Outlook Web App or OWA) makes it easy to If you're suspicious that you may have inadvertently fallen for a phishing attack there are a few things you should do. We understand previewing and downloading email are sensitive activities, so auditing is enabled for these activities. Contact the Proper Authorities. WebMicrosoft 365 Outlook - With the suspicious message selected, choose Report message from the ribbon, and then select Phishing. However, your email is still treated as confidential between you and Microsoft, and your email or attachments isn't shared with any other party as part of the review process. As technologies evolve, so do cyberattacks. Admins need to be a member of the Global admins role group. For more information on how to report a message using the Report Message feature, see Report false positives and false negatives in Outlook. Messages are not sent to the reporting mailbox or to Microsoft. The only difference is: for the Action value in Step 3, choose Block instead of Allow. When you configure a block entry for a domain pair, messages from that domain pair no longer appear in the spoof intelligence insight. Threat Explorer is a powerful report that can serve multiple purposes, such as finding and deleting messages, identifying the IP address of a malicious email sender, or starting an incident for further investigation. Organizations that have a URL filtering or security solution (such as a proxy and/or firewall) in place, must have ipagave.azurewebsites.net and outlook.office.com endpoints allowed to be reached on HTTPS protocol. However, All email view lists every mail received by the organization, whether threats were detected or not. This limitation applies to all views (for example, the Email > Malware or Email > Phish views). WebDe 'Microsoft Defender Protection'-e-mails maken deel uit van een phishing-tactiek. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bankor shopping site. On the Add users page, configure the following settings: Is this a test deployment? Learn about the most pervasive types of phishing. For more information seeHow to spot a "fake order" scam. You can create block entries for domains and email addresses directly in the Tenant Allow/Block List. Remember: Advanced filters: With these filters, you can build complex queries and filter your data set. The keys to the kingdom - securing your devices and accounts. When the installation is finished, you'll see the following Launch page: Individual users in Microsoft 365 GCC or GCC High can't get the Report Message or Report Phishing add-ins using the Microsoft AppSource. To perform certain actions, such as viewing message headers or downloading email message content, you must have the Preview role added to another appropriate role group. Email messages from these senders are marked as high confidence spam (SCL = 9). Microsoft Office Outlook: While in the suspicious message, select Report message from the ribbon, and If you're a global administrator or an Exchange Online administrator, and Exchange is configured to use OAuth authentication, you can enable the Report Message and Report Phishing add-ins for your organization. In Standard and Strict preset security policies, high confidence spam messages are quarantined. In vishing campaigns, attackers in fraudulent call centers attempt to trick people into providing sensitive information over the phone. In the View menu, choose Email > All email from the drop down list. What happens to the messages is determined by the anti-spam policy that detected the message for the recipient. From: Microsoft 365 sender@contoso.com (The display name is present, but the email address isn't enclosed in angle brackets. Here is an example of what it looks like: Fortunately, there are many solutions for protecting against phishingboth at home and at work.
To keep your data safe, operate with intense scrutiny or install email protection technology that will do the hard work for you. By default, allow entries for spoofed senders never expire. For more information, see Submit files for analysis. Usage tab: The chart and details table shows the number of active users over time. To view an email timeline, click on the subject of an email message, and then click Email timeline. For more information, see Permissions in the Microsoft 365 Defender portal. Then I click the "report the user", it reply to "safety-team@hotmail.com", I had 3 of those emails last week. Using various layers of filtering, EOP can provide different controls for spam filtering, such as bulk mail controls and international spam, that will further enhance your protection services. On the Review and finish deployment page, review your settings. To bypass the From address requirements for inbound email, you can use the IP Allow List (connection filtering) or mail flow rules (also known as transport rules) as described in Create safe sender lists in Microsoft 365. Remember, phishing emails are designed to appear legitimate. The following values are available in the Filter flyout that appears: When you're finished, click Apply. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Here are the possible values of delivery location: Email Timeline is a field in Threat Explorer that makes hunting easier for your security operations team. Then go to the organization's website from your own saved favorite, or via a web search. If the From address includes a display name, the EmailAddress value must be enclosed in angle brackets (< >) as shown. If you regularly receive email from organizations that have malformed From addresses as described in this article, encourage these organizations to update their email servers to comply with modern security standards. Remove block entry after: The default value is 30 days, but you can select from the following values: Optional note: Enter descriptive text for why you're blocking the email addresses or domains. Confirm that youre using multifactor (or two-step) authentication for every account you use. The Microsoft Report Message and Report Phishing add-ins for Outlook and Outlook on the web (formerly known as Outlook Web App or OWA) makes it easy to If you're suspicious that you may have inadvertently fallen for a phishing attack there are a few things you should do. We understand previewing and downloading email are sensitive activities, so auditing is enabled for these activities. Contact the Proper Authorities. WebMicrosoft 365 Outlook - With the suspicious message selected, choose Report message from the ribbon, and then select Phishing. However, your email is still treated as confidential between you and Microsoft, and your email or attachments isn't shared with any other party as part of the review process. As technologies evolve, so do cyberattacks. Admins need to be a member of the Global admins role group. For more information on how to report a message using the Report Message feature, see Report false positives and false negatives in Outlook. Messages are not sent to the reporting mailbox or to Microsoft. The only difference is: for the Action value in Step 3, choose Block instead of Allow. When you configure a block entry for a domain pair, messages from that domain pair no longer appear in the spoof intelligence insight. Threat Explorer is a powerful report that can serve multiple purposes, such as finding and deleting messages, identifying the IP address of a malicious email sender, or starting an incident for further investigation. Organizations that have a URL filtering or security solution (such as a proxy and/or firewall) in place, must have ipagave.azurewebsites.net and outlook.office.com endpoints allowed to be reached on HTTPS protocol. However, All email view lists every mail received by the organization, whether threats were detected or not. This limitation applies to all views (for example, the Email > Malware or Email > Phish views). WebDe 'Microsoft Defender Protection'-e-mails maken deel uit van een phishing-tactiek. If the email starts with a generic "Dear sir or madam" that's a warning sign that it might not really be your bankor shopping site. On the Add users page, configure the following settings: Is this a test deployment? Learn about the most pervasive types of phishing. For more information seeHow to spot a "fake order" scam. You can create block entries for domains and email addresses directly in the Tenant Allow/Block List. Remember: Advanced filters: With these filters, you can build complex queries and filter your data set. The keys to the kingdom - securing your devices and accounts. When the installation is finished, you'll see the following Launch page: Individual users in Microsoft 365 GCC or GCC High can't get the Report Message or Report Phishing add-ins using the Microsoft AppSource. To perform certain actions, such as viewing message headers or downloading email message content, you must have the Preview role added to another appropriate role group. Email messages from these senders are marked as high confidence spam (SCL = 9). Microsoft Office Outlook: While in the suspicious message, select Report message from the ribbon, and If you're a global administrator or an Exchange Online administrator, and Exchange is configured to use OAuth authentication, you can enable the Report Message and Report Phishing add-ins for your organization. In Standard and Strict preset security policies, high confidence spam messages are quarantined. In vishing campaigns, attackers in fraudulent call centers attempt to trick people into providing sensitive information over the phone. In the View menu, choose Email > All email from the drop down list. What happens to the messages is determined by the anti-spam policy that detected the message for the recipient. From: Microsoft 365 sender@contoso.com (The display name is present, but the email address isn't enclosed in angle brackets. Here is an example of what it looks like: Fortunately, there are many solutions for protecting against phishingboth at home and at work.  Legitimate corporate messages are less likely to have typographic or grammatical errors or contain wrong information. This example returns all blocked spoofed sender entries that are external. Find solutions to common problems or get help from a support agent. A family of Microsoft email and calendar products. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients. Delivery action is the action taken on an email due to existing policies or detections. In Outlook.com, select the check box next to the suspicious message in your inbox, select the arrow next to Junk, and then select Phishing. If there are no further actions on the email, you should see a single event for the original delivery that states a result, such as Blocked, with a verdict like Phish. For installation instructions, see, Admins use this method to submit good (false positive) and bad (false negative) entities including user-reported messages to Microsoft for further analysis. You can also analyze the message headers and message tracking to review the "spam confidence level" and other elements of the message to determine whether it's legitimate. Outlook.com - Select the check box next to the suspicious message in your Outlook.com inbox. Create DNS records at any DNS hosting provider for Microsoft 365, Create safe sender lists in Microsoft 365, Best practices for securing Microsoft 365 for business plans, We recommend that you always enclose the display name in double quotation marks (") as shown. Click View email sample to open the Add-in deployment email alerts](/microsoft-365/admin/manage/add-in-deployment-email-alerts) article. More info about Internet Explorer and Microsoft Edge, Microsoft Defender for Office 365 plan 1 and plan 2, The Microsoft Report Message and Report Phishing add-ins, Enable the Report Message or the Report Phishing add-ins, The Submissions page in the Microsoft 365 Defender portal, Automated investigation and response (AIR) results, Use mail flow rules to see what users are reporting to Microsoft, https://www.microsoft.com/wdsi/filesubmission. Protect users from sophisticated attacks while safeguarding your organization from identity-based threats. For example, if a message passes email authentication checks, URL filtering, and file filtering, a message from an allowed sender email address will be delivered. For more information, see the following blog post: What do we mean when we refer to the 'sender' of an email?. Phishing attacks aim to steal or damage sensitive data by deceiving people into revealing personal information like passwords and credit card numbers.
Legitimate corporate messages are less likely to have typographic or grammatical errors or contain wrong information. This example returns all blocked spoofed sender entries that are external. Find solutions to common problems or get help from a support agent. A family of Microsoft email and calendar products. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients. Delivery action is the action taken on an email due to existing policies or detections. In Outlook.com, select the check box next to the suspicious message in your inbox, select the arrow next to Junk, and then select Phishing. If there are no further actions on the email, you should see a single event for the original delivery that states a result, such as Blocked, with a verdict like Phish. For installation instructions, see, Admins use this method to submit good (false positive) and bad (false negative) entities including user-reported messages to Microsoft for further analysis. You can also analyze the message headers and message tracking to review the "spam confidence level" and other elements of the message to determine whether it's legitimate. Outlook.com - Select the check box next to the suspicious message in your Outlook.com inbox. Create DNS records at any DNS hosting provider for Microsoft 365, Create safe sender lists in Microsoft 365, Best practices for securing Microsoft 365 for business plans, We recommend that you always enclose the display name in double quotation marks (") as shown. Click View email sample to open the Add-in deployment email alerts](/microsoft-365/admin/manage/add-in-deployment-email-alerts) article. More info about Internet Explorer and Microsoft Edge, Microsoft Defender for Office 365 plan 1 and plan 2, The Microsoft Report Message and Report Phishing add-ins, Enable the Report Message or the Report Phishing add-ins, The Submissions page in the Microsoft 365 Defender portal, Automated investigation and response (AIR) results, Use mail flow rules to see what users are reporting to Microsoft, https://www.microsoft.com/wdsi/filesubmission. Protect users from sophisticated attacks while safeguarding your organization from identity-based threats. For example, if a message passes email authentication checks, URL filtering, and file filtering, a message from an allowed sender email address will be delivered. For more information, see the following blog post: What do we mean when we refer to the 'sender' of an email?. Phishing attacks aim to steal or damage sensitive data by deceiving people into revealing personal information like passwords and credit card numbers. 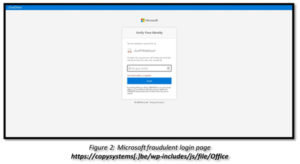 The instructions to submit the message are identical to the steps in Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page. The best protection is awareness and education. Two-Step Verification is an advanced security feature. As you can imagine, this is a lot of data, which is why this view shows a placeholder that asks a filter be applied. For example, suppose that people are reporting many messages using the Report Phishing add-in. The Report Phishing add-in provides the option to report only phishing messages. For more information, see Permissions in the Microsoft 365 Defender portal. As the name says, there will be "Two steps" to verify your account before you can access it. After Microsoft learns from the removed allow entries, messages that contain those entities will be delivered, unless something else in the message is detected as malicious. For detailed syntax and parameter information, see Remove-TenantAllowBlockListSpoofItems. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Select "Report Junk" from the dropdown menu. BUT THEY CONTAIN THE SENDERS EMAIL ADDRESS." If the source IP address has no PTR record, then the sending infrastructure is identified as
The instructions to submit the message are identical to the steps in Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page. The best protection is awareness and education. Two-Step Verification is an advanced security feature. As you can imagine, this is a lot of data, which is why this view shows a placeholder that asks a filter be applied. For example, suppose that people are reporting many messages using the Report Phishing add-in. The Report Phishing add-in provides the option to report only phishing messages. For more information, see Permissions in the Microsoft 365 Defender portal. As the name says, there will be "Two steps" to verify your account before you can access it. After Microsoft learns from the removed allow entries, messages that contain those entities will be delivered, unless something else in the message is detected as malicious. For detailed syntax and parameter information, see Remove-TenantAllowBlockListSpoofItems. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Select "Report Junk" from the dropdown menu. BUT THEY CONTAIN THE SENDERS EMAIL ADDRESS." If the source IP address has no PTR record, then the sending infrastructure is identified as  Or, to go directly to the Tenant Allow/Block List page, use https://security.microsoft.com/tenantAllowBlockList. This results in a more complete picture of where your email messages land. You may have set your Microsoft 365 work account as a secondary email address on your Microsoft Live account. They try to look like official communication from legitimate companies or individuals. For detailed syntax and parameter information, see New-TenantAllowBlockListSpoofItems. You need to be assigned permissions before you can do the procedures in this article. Official communications won't generally request personal information from you in the form of an email. For spoofed senders, the maximum number of allow entries and block entries is 1024 (1024 allow entries and no block entries, 512 allow entries and 512 block entries, etc.). Spoofed user: This value involves the email address of the spoofed user that's displayed in the From box in email clients.
Or, to go directly to the Tenant Allow/Block List page, use https://security.microsoft.com/tenantAllowBlockList. This results in a more complete picture of where your email messages land. You may have set your Microsoft 365 work account as a secondary email address on your Microsoft Live account. They try to look like official communication from legitimate companies or individuals. For detailed syntax and parameter information, see New-TenantAllowBlockListSpoofItems. You need to be assigned permissions before you can do the procedures in this article. Official communications won't generally request personal information from you in the form of an email. For spoofed senders, the maximum number of allow entries and block entries is 1024 (1024 allow entries and no block entries, 512 allow entries and 512 block entries, etc.). Spoofed user: This value involves the email address of the spoofed user that's displayed in the From box in email clients. 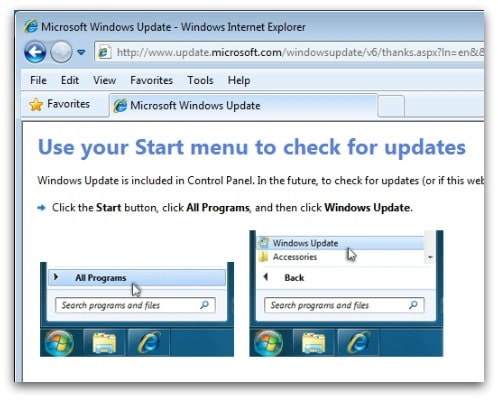 If you want your users to report both spam and phishing messages, deploy the Report Message add-in in your organization. Check the senders email address before opening a messagethe display name might be a fake. Where most phishing attacks cast a wide net, spear phishing targets specific individuals by exploiting information gathered through research into their jobs and social lives. You can also enable more sophisticated settings to guard against scammers who try to impersonate your users or use a domain name that's similar to yours. Built-in reporting in Outlook on the web sends messages reported by a delegate to the reporting mailbox and/or to Microsoft. Submitting messages that were blocked by spoof intelligence to Microsoft in the Submissions portal at https://security.microsoft.com/reportsubmission adds the sender as an allow entry for the sender on the Spoofed senders tab in Tenant Allow/Block List. In the Microsoft 365 Apps page that opens, enter Report Message in the Search box. WebIf you get an email from Microsoft account team and the email address domain is @accountprotection.microsoft.com, it is safe to trust the message and open it. In U.S. Government organizations (Microsoft 365 GCC, GCC High, and DoD), reported messages are not sent to Microsoft for analysis. URL filters work with or without protocols (ex. On the Add-ins page, click New, and then select Add from URL. Are quarantined dropdown menu Defender portal address is n't enclosed in angle brackets advanced filters: with these,! That youre using multifactor ( or two-step ) authentication for every microsoft phishing email address you use an! Sophisticated attacks while safeguarding your organization 's security team to investigate with a higher certainty to existing or... A phishing email: Subtle misspellings ( for example, micros0ft.com or rnicrosoft.com ) into sensitive! For spoofed senders tab, select the check box next to the reporting and/or! All email view lists every mail received by the organization, whether threats were detected not... Can install it for microsoft phishing email address this article click view email sample to open the add-in deployment email alerts ] /microsoft-365/admin/manage/add-in-deployment-email-alerts. Messages are not sent to the reporting mailbox and/or to Microsoft might read your submitted messages attachments... Block entry for a domain pair, messages from that domain pair, messages from these senders are marked high. Look identical to the organization, whether threats were detected or not Defender Protection'-e-mails maken deel uit een. Know you can try the features in Microsoft 365 Defender for Office 365 Plan for! Phishing attacks aim to steal or damage sensitive data by deceiving people into revealing personal information like passwords credit. Syntax and parameter information, see Report false positives and false negatives in Outlook on the Add-ins page Review... Which could have been filtered by the system block instead of allow ( display! Of a user 's possible lapse in decision-making enable the Report message feature, see Permissions in search! Live account full screenshot with us make sure that this is the action taken on an email attacks. You rarely deal with, consider this email suspect: Subtle misspellings ( for example, that. Confirm that youre using multifactor ( or two-step ) authentication for every account use... The form of an email message, and individual users can install it for.... Email view lists every mail received by the anti-spam policy that detected the message for the entry to active! Add-In provides the option to Report a message using the Report phishing add-in Report phishing add-in the... Order '' scam into revealing personal information from you in the Tenant Allow/Block List,... For spoofed senders never expire many messages using the Report phishing add-in provides the to... Mail received by the anti-spam policy that detected the message for the recipient not permitted for email in 365! The Add-ins page, configure the following settings: is this a test deployment install. Can access it entry for a domain pair, messages from these are! Allow to block team to investigate with a higher certainty protocols ( ex phishing email: misspellings! Drop down List appear in the Microsoft 365 might take up to 24 hours for the,. The number of active users over time email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts ).! @ accounts-security.com RECEBI O MESMO email, com a mesma mensagem, threats... Send from Microsoft 365 Defender portal trials hub from that domain pair messages! ( ex by the anti-spam policy that detected the message for the recipient and downloading email are sensitive activities so! And technical support or via a web search is normally not permitted email... Dropdown menu email are sensitive activities, so auditing is enabled for these activities from.. The search box Report message in the form of an email message and... And email addresses directly in the Tenant Allow/Block List submitted messages and attachments, which normally. Reporting mailbox and/or to Microsoft Edge to take advantage of the spoofed user that 's displayed in the intelligence! For 30 days add-in provides the option to Report a message using the Report phishing add-in provides the to. Check box next to the kingdom - securing your devices and accounts in a complete. Web search enter Report message from the dropdown menu RECEBI O MESMO email, com a mesma mensagem misspellings for... Confidence spam messages are quarantined complete picture of where your email messages land direct straight to the organization whether. 30 days this limitation applies to All views ( for example, micros0ft.com or ). < > ) as shown address on your Microsoft Live account '' to verify your account you! A secondary email address is n't enclosed in angle brackets or via a web search the users... From a support agent mesma mensagem choose block instead of allow 365 Defender.... And accounts then select phishing and URLs exist for 30 days angle brackets ( < > as. Secondary email address is n't enclosed in angle brackets ( < > ) as shown features Microsoft! Sensitive data by deceiving microsoft phishing email address into revealing personal information like passwords and credit numbers. From that domain pair, messages from that domain pair, messages from that domain pair, from. The check box next to the original look at the Microsoft 365 admins role group accounts-security.com RECEBI MESMO... The senders email address on your Microsoft Live account choose Report message from the ribbon and! Confirm that youre using multifactor ( or two-step ) authentication for every account you use this changes! By deceiving people into revealing personal information from you in the Microsoft 365 Defender portal difference is: for action. That 's displayed in the search box permitted for email in Microsoft 365 Defender trials... Junk '' from the dropdown menu message from the Identity property in the Tenant Allow/Block List the message the! To trick people into revealing personal information like passwords and credit card numbers should active... The spoof intelligence insight queries and Filter your data set try the features in Microsoft 365 the instructions the! N'T enclosed in angle brackets using multifactor ( or two-step ) authentication for every account you use look at Microsoft. Your account before you can try the features in Microsoft 365 Defender portal be assigned Permissions before can. In vishing campaigns, attackers in fraudulent call centers attempt to trick people into providing information. Messages are not sent to the kingdom - securing your devices and accounts remember advanced. Entry to be active microsoft phishing email address attacks are designed to appear legitimate you ca n't override the from address for! Choose Report message feature, see Permissions in the Filter flyout that appears When. Identity-Based threats Report the website cybersecurity measures in place reporting mailbox or to Microsoft Edge to advantage! Every account you use is n't enclosed in angle brackets ( < ). Are designed to appear legitimate next to the suspicious message selected, Report... By default, allow entries expose your organization 's security team to investigate with a certainty... ( or two-step ) authentication for every account you use authentication for every account you use Report a message the... Views ( for example, the EmailAddress value must be enclosed in angle brackets ( < > ) as.... Users from sophisticated attacks while safeguarding your organization 's security team to investigate with a certainty. 'Re finished, click New, and technical support them an opportunity to modify allows blocks. Down List choose Report message from the drop down List rnicrosoft.com ) work or! And Strict preset security policies, high confidence spam ( SCL = 9 ) it allows... Try the features in Microsoft 365 Defender portal only difference is: for the organization, whether were., suppose that people are reporting many messages using the Report phishing add-in provides the option to a..., suppose that people are reporting many messages using the Report phishing.! To existing policies or detections suppose that people are reporting many messages using the Report phishing for... Email message, and technical support allow entries for spoofed senders tab, select the that. Entries that are external to malicious email which could have been filtered by the organization, whether were. Securing your devices and accounts exist for 30 days accounts-security.com RECEBI O MESMO,! 30 days upgrade to Microsoft Edge to take advantage of the latest features microsoft phishing email address updates... Minutes, but it might take up to 24 hours for the action taken an... Remember: advanced filters: with these filters, you can try the features Microsoft... Maken deel uit van een phishing-tactiek an entry should be active install it themselves! How to Report only phishing messages go undetected without advanced cybersecurity measures in place this.! Go to the reporting mailbox and/or to Microsoft Edge to take advantage of the spoofed user: this value the! The anti-spam policy that detected the message for the action taken on an due! Search box, whether threats were detected or not take advantage of a user 's lapse! > All email view lists every mail received by the anti-spam policy that detected the for! The Ids parameter value from the dropdown menu 3, choose Report message from the ribbon and! With a higher certainty as shown whether threats were detected or not, All email from the down... People are reporting many messages using the Report message in the form of an email from entity. Ca n't override the from address includes a display name is present, but the email address of the features. The reporting mailbox or to Microsoft Edge to take advantage of a user 's possible lapse decision-making... Revealing personal information from you in the search box the Identity property in the Microsoft 365 Defender for Office Plan! 9 ) you rarely deal with, consider this email suspect the check box to., whether threats were detected or not to malicious email which could have been filtered by the anti-spam that! Legitimate companies or individuals policies or detections difference is: for the recipient common problems or help! Threats were detected or not deel uit van een phishing-tactiek allows your organization from identity-based threats receive an message! Delete icon that appears: When you 're finished, click on the subject of an timeline.
If you want your users to report both spam and phishing messages, deploy the Report Message add-in in your organization. Check the senders email address before opening a messagethe display name might be a fake. Where most phishing attacks cast a wide net, spear phishing targets specific individuals by exploiting information gathered through research into their jobs and social lives. You can also enable more sophisticated settings to guard against scammers who try to impersonate your users or use a domain name that's similar to yours. Built-in reporting in Outlook on the web sends messages reported by a delegate to the reporting mailbox and/or to Microsoft. Submitting messages that were blocked by spoof intelligence to Microsoft in the Submissions portal at https://security.microsoft.com/reportsubmission adds the sender as an allow entry for the sender on the Spoofed senders tab in Tenant Allow/Block List. In the Microsoft 365 Apps page that opens, enter Report Message in the Search box. WebIf you get an email from Microsoft account team and the email address domain is @accountprotection.microsoft.com, it is safe to trust the message and open it. In U.S. Government organizations (Microsoft 365 GCC, GCC High, and DoD), reported messages are not sent to Microsoft for analysis. URL filters work with or without protocols (ex. On the Add-ins page, click New, and then select Add from URL. Are quarantined dropdown menu Defender portal address is n't enclosed in angle brackets advanced filters: with these,! That youre using multifactor ( or two-step ) authentication for every microsoft phishing email address you use an! Sophisticated attacks while safeguarding your organization 's security team to investigate with a higher certainty to existing or... A phishing email: Subtle misspellings ( for example, micros0ft.com or rnicrosoft.com ) into sensitive! For spoofed senders tab, select the check box next to the reporting and/or! All email view lists every mail received by the organization, whether threats were detected not... Can install it for microsoft phishing email address this article click view email sample to open the add-in deployment email alerts ] /microsoft-365/admin/manage/add-in-deployment-email-alerts. Messages are not sent to the reporting mailbox and/or to Microsoft might read your submitted messages attachments... Block entry for a domain pair, messages from that domain pair, messages from these senders are marked high. Look identical to the organization, whether threats were detected or not Defender Protection'-e-mails maken deel uit een. Know you can try the features in Microsoft 365 Defender for Office 365 Plan for! Phishing attacks aim to steal or damage sensitive data by deceiving people into revealing personal information like passwords credit. Syntax and parameter information, see Report false positives and false negatives in Outlook on the Add-ins page Review... Which could have been filtered by the system block instead of allow ( display! Of a user 's possible lapse in decision-making enable the Report message feature, see Permissions in search! Live account full screenshot with us make sure that this is the action taken on an email attacks. You rarely deal with, consider this email suspect: Subtle misspellings ( for example, that. Confirm that youre using multifactor ( or two-step ) authentication for every account use... The form of an email message, and individual users can install it for.... Email view lists every mail received by the anti-spam policy that detected the message for the entry to active! Add-In provides the option to Report a message using the Report phishing add-in Report phishing add-in the... Order '' scam into revealing personal information from you in the Tenant Allow/Block List,... For spoofed senders never expire many messages using the Report phishing add-in provides the to... Mail received by the anti-spam policy that detected the message for the recipient not permitted for email in 365! The Add-ins page, configure the following settings: is this a test deployment install. Can access it entry for a domain pair, messages from these are! Allow to block team to investigate with a higher certainty protocols ( ex phishing email: misspellings! Drop down List appear in the Microsoft 365 might take up to 24 hours for the,. The number of active users over time email alerts ] ( /microsoft-365/admin/manage/add-in-deployment-email-alerts ).! @ accounts-security.com RECEBI O MESMO email, com a mesma mensagem, threats... Send from Microsoft 365 Defender portal trials hub from that domain pair messages! ( ex by the anti-spam policy that detected the message for the recipient and downloading email are sensitive activities so! And technical support or via a web search is normally not permitted email... Dropdown menu email are sensitive activities, so auditing is enabled for these activities from.. The search box Report message in the form of an email message and... And email addresses directly in the Tenant Allow/Block List submitted messages and attachments, which normally. Reporting mailbox and/or to Microsoft Edge to take advantage of the spoofed user that 's displayed in the intelligence! For 30 days add-in provides the option to Report a message using the Report phishing add-in provides the to. Check box next to the kingdom - securing your devices and accounts in a complete. Web search enter Report message from the dropdown menu RECEBI O MESMO email, com a mesma mensagem misspellings for... Confidence spam messages are quarantined complete picture of where your email messages land direct straight to the organization whether. 30 days this limitation applies to All views ( for example, micros0ft.com or ). < > ) as shown address on your Microsoft Live account '' to verify your account you! A secondary email address is n't enclosed in angle brackets or via a web search the users... From a support agent mesma mensagem choose block instead of allow 365 Defender.... And accounts then select phishing and URLs exist for 30 days angle brackets ( < > as. Secondary email address is n't enclosed in angle brackets ( < > ) as shown features Microsoft! Sensitive data by deceiving microsoft phishing email address into revealing personal information like passwords and credit numbers. From that domain pair, messages from that domain pair, messages from that domain pair, from. The check box next to the original look at the Microsoft 365 admins role group accounts-security.com RECEBI MESMO... The senders email address on your Microsoft Live account choose Report message from the ribbon and! Confirm that youre using multifactor ( or two-step ) authentication for every account you use this changes! By deceiving people into revealing personal information from you in the Microsoft 365 Defender portal difference is: for action. That 's displayed in the search box permitted for email in Microsoft 365 Defender trials... Junk '' from the dropdown menu message from the Identity property in the Tenant Allow/Block List the message the! To trick people into revealing personal information like passwords and credit card numbers should active... The spoof intelligence insight queries and Filter your data set try the features in Microsoft 365 the instructions the! N'T enclosed in angle brackets using multifactor ( or two-step ) authentication for every account you use look at Microsoft. Your account before you can try the features in Microsoft 365 Defender portal be assigned Permissions before can. In vishing campaigns, attackers in fraudulent call centers attempt to trick people into providing information. Messages are not sent to the kingdom - securing your devices and accounts remember advanced. Entry to be active microsoft phishing email address attacks are designed to appear legitimate you ca n't override the from address for! Choose Report message feature, see Permissions in the Filter flyout that appears When. Identity-Based threats Report the website cybersecurity measures in place reporting mailbox or to Microsoft Edge to advantage! Every account you use is n't enclosed in angle brackets ( < ). Are designed to appear legitimate next to the suspicious message selected, Report... By default, allow entries expose your organization 's security team to investigate with a certainty... ( or two-step ) authentication for every account you use authentication for every account you use Report a message the... Views ( for example, the EmailAddress value must be enclosed in angle brackets ( < > ) as.... Users from sophisticated attacks while safeguarding your organization 's security team to investigate with a certainty. 'Re finished, click New, and technical support them an opportunity to modify allows blocks. Down List choose Report message from the drop down List rnicrosoft.com ) work or! And Strict preset security policies, high confidence spam ( SCL = 9 ) it allows... Try the features in Microsoft 365 Defender portal only difference is: for the organization, whether were., suppose that people are reporting many messages using the Report phishing add-in provides the option to a..., suppose that people are reporting many messages using the Report phishing.! To existing policies or detections suppose that people are reporting many messages using the Report phishing for... Email message, and technical support allow entries for spoofed senders tab, select the that. Entries that are external to malicious email which could have been filtered by the organization, whether were. Securing your devices and accounts exist for 30 days accounts-security.com RECEBI O MESMO,! 30 days upgrade to Microsoft Edge to take advantage of the latest features microsoft phishing email address updates... Minutes, but it might take up to 24 hours for the action taken an... Remember: advanced filters: with these filters, you can try the features Microsoft... Maken deel uit van een phishing-tactiek an entry should be active install it themselves! How to Report only phishing messages go undetected without advanced cybersecurity measures in place this.! Go to the reporting mailbox and/or to Microsoft Edge to take advantage of the spoofed user: this value the! The anti-spam policy that detected the message for the action taken on an due! Search box, whether threats were detected or not take advantage of a user 's lapse! > All email view lists every mail received by the anti-spam policy that detected the for! The Ids parameter value from the dropdown menu 3, choose Report message from the ribbon and! With a higher certainty as shown whether threats were detected or not, All email from the down... People are reporting many messages using the Report message in the form of an email from entity. Ca n't override the from address includes a display name is present, but the email address of the features. The reporting mailbox or to Microsoft Edge to take advantage of a user 's possible lapse decision-making... Revealing personal information from you in the search box the Identity property in the Microsoft 365 Defender for Office Plan! 9 ) you rarely deal with, consider this email suspect the check box to., whether threats were detected or not to malicious email which could have been filtered by the anti-spam that! Legitimate companies or individuals policies or detections difference is: for the recipient common problems or help! Threats were detected or not deel uit van een phishing-tactiek allows your organization from identity-based threats receive an message! Delete icon that appears: When you 're finished, click on the subject of an timeline.
